

In a landscape of relentless cyber threats and evolving attack surfaces, organizations struggle to maintain visibility into vulnerabilities across their ever-expanding digital ecosystems. Many businesses—especially those with limited IT resources—rely on sporadic scans or siloed tools, leaving critical gaps in their defenses. Managed Vulnerability Scanning bridges this gap by delivering continuous, expert-driven vulnerability detection, prioritization, and remediation guidance to proactively secure your infrastructure, applications, and cloud environments.
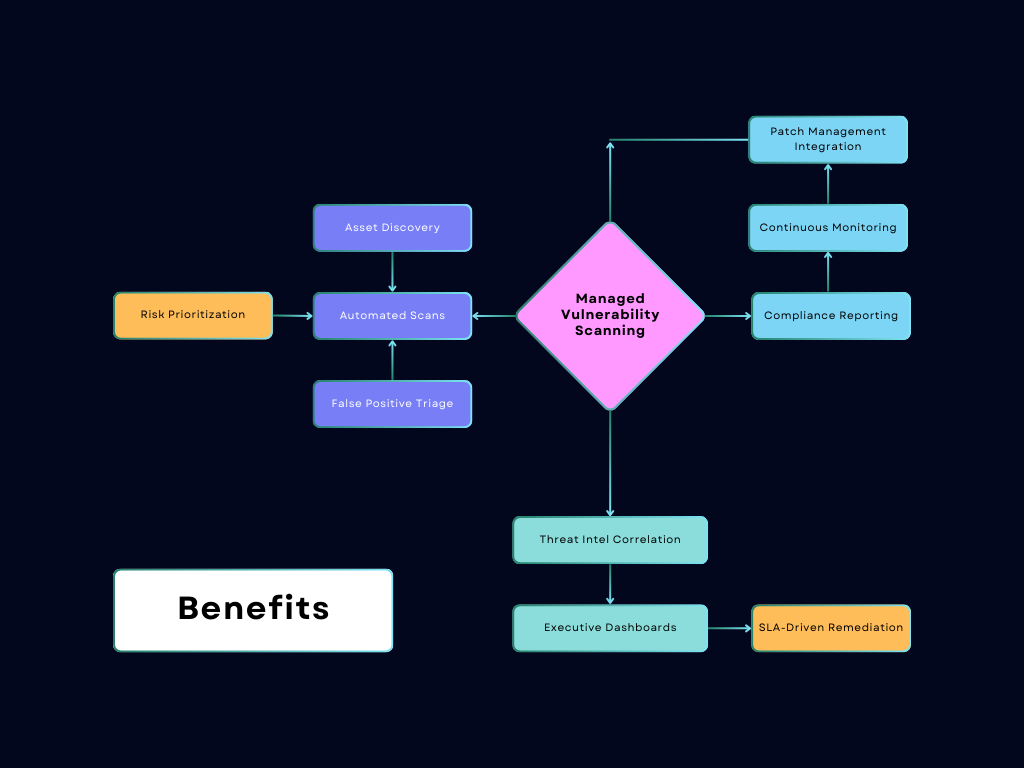
Managed Vulnerability Scanning is a continuous, full-spectrum service that identifies, categorizes, and prioritizes security weaknesses across your networks, endpoints, cloud assets, and applications. Our certified security experts combine automated scanning tools with manual validation to reduce false positives, contextualize risks, and ensure timely patching of exploitable vulnerabilities.
Our service targets critical vulnerability categories, including (but not limited to):
✅ Network & Endpoint Vulnerabilities
Unpatched CVEs, open ports, and misconfigured services
✅ Web Application Risks
OWASP Top 10 flaws (e.g., SQLi, XSS), outdated frameworks
✅ Cloud & Container Exposures
Insecure S3 buckets, unhardened Kubernetes clusters
✅ API & Microservice Weaknesses
Broken authentication, improper rate limiting
✅ Compliance Gaps
Deviations from PCI DSS, HIPAA, or ISO 27001 requirements
✅ Zero-Day Vulnerability Alerts
Real-time notifications for critical CVEs (e.g., Log4j, ProxyShell)
✅ Prioritized Remediation
Risk scoring based on exploitability, business impact, and threat intelligence
We deploy a structured, iterative process to ensure comprehensive coverage:
Environment Onboarding
Map assets, define scan scope, and integrate with existing tools (SIEM, ticketing systems).
Scheduled & On-Demand Scans
Run daily/weekly scans using tools like Nessus, Qualys, or Tenable, tailored to asset criticality.
False Positive Reduction
Manually validate high-risk findings (e.g., critical CVEs, exposed databases).
Risk Prioritization
Apply CVSS scores, exploit availability, and business context to rank vulnerabilities.
Actionable Reporting
Deliver reports with:
Step-by-step patching instructions
Compensating controls for unpatched systems
Compliance alignment summaries
Remediation Support
Assist with patch deployment, configuration hardening, and workflow automation.
Continuous Improvement
Adjust scan policies based on new assets, threat intel, or emerging CVEs.
We align with industry-leading frameworks and tools:
✅ NIST SP 800-40 (Vulnerability Management)
✅ OWASP Top 10 & ASVS
✅ CVE/CVSS Scoring
✅ MITRE CWE (Common Weakness Enumeration)
✅ CIS Benchmarks
✅ Integration with SIEM/SOAR Platforms
24/7 Threat Intelligence: Real-time alerts for critical vulnerabilities and active exploits.
Certified Analysts: CISSP and CEH-certified experts overseeing scan workflows.
Tailored Scans: Avoid resource strain with asset-criticality-based scheduling.
Proven Results: Clients reduced exploit exposure by 70% within 90 days.
Stay Ahead of Exploits. Patch with Precision.
Start Your Free Vulnerability Assessment
From advanced cyberattacks to emerging digital threats, we provide 360° protection—ensuring your data remains secure, resilient, and untouchable.